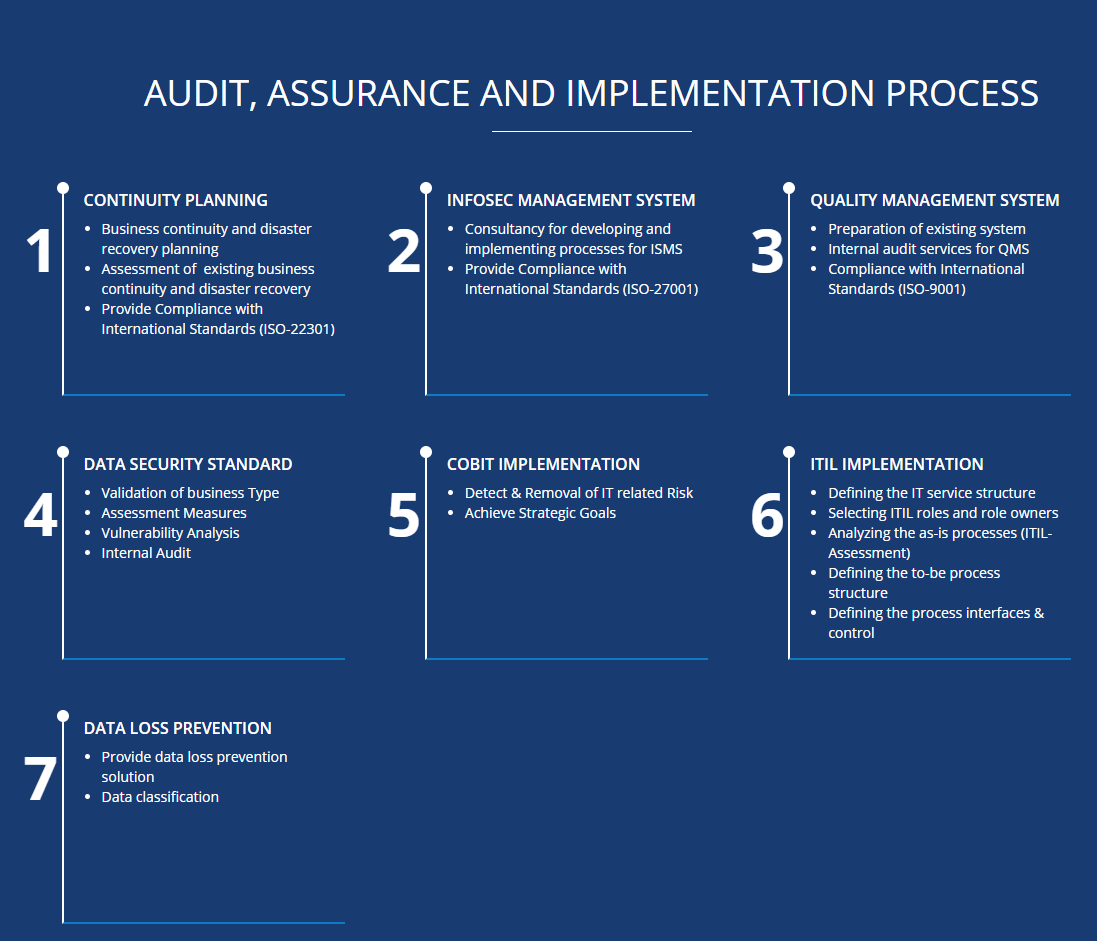
OUR APPROACH
BlackHatWing enable organizations to be proactively planning for their business continuity and any possible disaster recovery. Our experienced consultants with their backgrounds as CISA, CISSP, BS25999, ISO 27001 Lead Auditor, ISO 9001, 27001, 20000 Internal Auditors, develop standard practices for organizations to avoid any possible disaster. We bring together decades of experience in the field of Information Security, Business Continuity Management, Service Management, Quality Management, Auditing, Process Improvement, Implementation, Consultancy & Trainings. ISMS ISO 27001 is standard for securing asset of organization and applicable to all sectors of industry and commerce working on electronic systems. This International Standard has been prepared to provide a model for establishing, implementing, operating, monitoring, reviewing, maintaining and improving ISMS. ISO 27001:2005 (ISMS) is a structured and systematic approach to manage information and information assets of the organization by maintaining confidentiality, integrity and availability. BlackHatWing works with their clients to establish a secure, transparent, organized working environment while sharing expert knowledge and experiences for developing and implementing processes for ISMS.
BlackHatWing works with their clients to establish a secure, transparent, organized working environment while sharing expert knowledge and experiences for developing and implementing processes for ISMS.
ISMS ISO 27001 is standard for securing asset of organization and applicable to all sectors of industry and commerce working on electronic systems. This International Standard has been prepared to provide a model for establishing, implementing, operating, monitoring, reviewing, maintaining and improving ISMS. ISO 27001:2005 (ISMS) is a structured and systematic approach to manage information and information assets of the organization by maintaining confidentiality, integrity and availability.